ElendiLabs
算法变更为“重大变更”,需通过 GN-10 路径申请。 • 时效策略: 考虑到 2026 年初 MDD 的处理积压,建议立即提交变更申请。在获批前,原有的 HKMD 编号在系统中仍视为有效,但仅限旧版本。 • Stage C 风险: 若要在 3 月后参与新标,必须确保新版本的变更已被 MDD 记录并更新在 MDIS 证书上,否则将被视为不合规。
Post your regulatory questions or request quotations from verified pharmaceutical consultants worldwide. Get matched with experts who specialize in your market.
May 17, 2025
Approximately 5 minutes
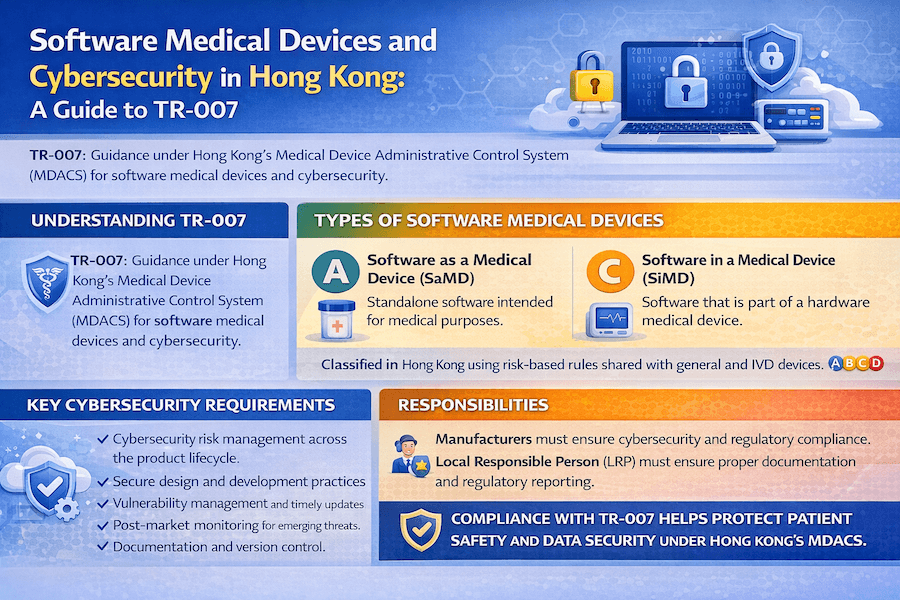
From our perspective, the rapid growth of digital health has put software at the very heart of medical innovation. In Hong Kong, the Medical Device Administrative Control System (MDACS) clearly recognizes the unique regulatory challenges and safety concerns that software brings. Technical Reference TR-007, specifically titled "Software Medical Devices and Cybersecurity," provides essential guidance for manufacturers and Local Responsible Persons (LRPs) on how to classify, develop, and protect the cybersecurity of software that acts as a medical device.
To our understanding, TR-007 aims to make sure that software medical devices are safe, work exactly as they're supposed to, and are well-protected against cyber threats. This document reflects global best practices in this constantly evolving field, which is crucial for Hong Kong medical device cybersecurity.
TR-007 clearly explains the difference between two main types of software we see in the medical world. Have you ever wondered if a health app on your phone counts as a medical device? Let's clarify!
Software as a Medical Device (SaMD):
Software in a Medical Device (SiMD):
The way SaMD and SiMD are classified under MDACS follows the same risk-based principles as other medical devices (you can find details in TR-003 for general devices and TR-006 for IVDMDs). The risk class depends on factors like what the software is intended to be used for, how important the information it provides is for diagnosis or treatment, and the potential impact on a patient's health if the information is wrong. TR-007 provides specific considerations and helpful flowcharts to guide you in correctly classifying your software, which is a critical step for software medical device regulation in Hong Kong.
Why is cybersecurity such a big deal for software medical devices? Because they can be vulnerable to unauthorized access, changes, or even being shut down, which could directly affect patient safety and the privacy of their sensitive health data. TR-007 strongly emphasizes that manufacturers must build cybersecurity measures into every single stage of their software medical devices' lifespan. Key cybersecurity requirements, as we understand them, include:
Manufacturers are ultimately responsible for making sure their software medical devices meet all the necessary basic principles and cybersecurity requirements. The Local Responsible Person (LRP) plays a crucial role in making sure this compliance is met, especially for foreign manufacturers. Based on our knowledge, the LRP must ensure that all the technical documentation accurately reflects strong cybersecurity practices, and that any cybersecurity issues that pop up after the product is on the market are quickly resolved and reported to the MDD. This continuous vigilance is vital for medical device regulatory compliance.
TR-007, in our opinion, serves as an indispensable guide. It helps ensure that we can fully enjoy the benefits of exciting software innovations in healthcare without ever compromising patient safety or the security of their sensitive data in Hong Kong.
We'll follow up with you personally.
ElendiLabs
算法变更为“重大变更”,需通过 GN-10 路径申请。 • 时效策略: 考虑到 2026 年初 MDD 的处理积压,建议立即提交变更申请。在获批前,原有的 HKMD 编号在系统中仍视为有效,但仅限旧版本。 • Stage C 风险: 若要在 3 月后参与新标,必须确保新版本的变更已被 MDD 记录并更新在 MDIS 证书上,否则将被视为不合规。
Anonymous
我们有一款基于云端的 AI 影像辅助诊断软件,已获美国 FDA 510(k) 许可。根据 2025 年修订版 TR-007,由于它涉及 AI 算法且在云端运行,其网络安全风险是否会自动将其分类等级从 Class II 提升至 Class III?在提交时,我们需要如何处理 TR-007 与 TR-008 的合规重叠
ElendiLabs
分类主要基于临床意图而非技术架构。但 TR-007 明确指出,如果网络安全漏洞可能导致错误的诊断结论并危及生命,分级会趋严。 • 重叠处理: 您需要提交一份合并的技术文件。在 TR-008 框架下,重点说明算法的透明度与数据集(Training/Validation/Test)的本地相关性;在 TR-007 下,重点说明云端数据传输的加密(AES-256)与身份验证机制。2026 年的 MDIS 系统要求必须同时勾选“AI 驱动”与“网络安全相关”两个标识。
Anonymous
我们的 SaMD 数据存储在 AWS 新加坡节点。在 2026 年的注册审核中,卫生署医疗器械分部 (MDD) 是否强制要求数据必须物理存储在香港境内?对于跨境传输医疗数据,LRP 是否需要向私隐专员公署 (PCPD) 备案?
ElendiLabs
香港目前并不强制要求数据本地化存储,但必须严格遵守 PDPO 的六项原则。 • 合规要求: 建议在技术文件中证明采取了“所有务实步骤”保护数据(DPP 4)。这包括与云供应商签订符合香港法律的数据处理协议 (DPA)。 • 备案建议: 虽然无需强制向 PCPD 备案,但 LRP 建议持有隐私影响评估 (PIA) 报告,以备 MDD 在 2026 年加强的现场审核中抽查。
Approximately 5 minutes
Adverse event reporting is a critical component of Hong Kong's Medical Device Administrative Control System (MDACS), aiming to enhance public health and safety. This article outlines the requirements and responsibilities of Local Responsible Persons (LRPs) in reporting adverse events related to listed medical devices, based on our insights.
Approximately 5 minutes
Complete guide to medical device regulations, classification, registration requirements and post-market surveillance in Hong Kong.
Approximately 5 minutes
Hong Kong's Medical Device Administrative Control System (MDACS) provides a robust, although currently voluntary, framework for regulating medical devices. This article explores the system's key features, including device classification, the listing process, the crucial role of Local Responsible Persons (LRPs), and its increasing importance for market access and public procurement, all from our insights and experience.
Approximately 5 minutes
This article details the application process for local medical device manufacturers seeking to be listed under Hong Kong's Medical Device Administrative Control System (MDACS), as guided by GN-08. It covers eligibility, quality management system requirements, and the submission process, all based on our insights and experience for effective Hong Kong medical device manufacturing.
Approximately 5 minutes
For entities importing medical devices into Hong Kong, the Medical Device Administrative Control System (MDACS) provides a voluntary listing scheme for importers, guided by GN-07. This article details the eligibility, application steps, and key requirements for listing as a medical device importer, based on our insights and experience for efficient Hong Kong medical device import.
Approximately 5 minutes
This article outlines the application process for medical device distributors seeking to be listed under Hong Kong's Medical Device Administrative Control System (MDACS), as detailed in GN-09. It covers eligibility, key requirements for documented procedures, and the submission process to enhance traceability and public safety, based on our insights.
Approximately 5 minutes
This article details the application process for listing Class B, C, and D In Vitro Diagnostic Medical Devices (IVDMDs) under Hong Kong's Medical Device Administrative Control System (MDACS), as guided by GN-06. It covers classification, eligibility, submission requirements, and the online application via MDIS, all based on our insights and experience for efficient IVDMD listing in Hong Kong.
Anonymous
我们已有一个旧版的软件表列号,但计划在 2026 年 2 月发布大版本更新(包含重大算法变更)。鉴于 Stage C 采购节点 在 3 月 23 日到期,我们应该申请‘变更 (Change Application)’还是重新注册?如果更新未能在截止日前获批,医院管理局 (HA) 的老用户能否继续使用旧版?